Hout Bay
Contents
Hout Bay WUG
The Hout Bay WUG is a small subWUG within Cape Town. It is not yet connected to CTWUG due to geographic difficulties, but as we gain more people we hope to eventually find a path out the valley and onto CTWUG. In the mean time we have established a small but very enthusiastic group of wuggers connected amongst each other with an extension to Kommetjie. This Wiki entry is simply a knowledge base specific to our area.
Meet the Hout Bay Wuggers
| Name | Nodes | ||
|---|---|---|---|
| Albert | earthling42 | ||
| Alistair | HB3-Ali | ||
| Aragon | Kush | Vertex | Republic |
| Armand | DarkStar | DeathStarCanteen | |
| Cobus | TROPiX | ||
| David | HitmanV-S | HitmanV-AP | |
| Denis | d3nis | ||
| Georg | Slangkop | Slangkop-AP | Riverside |
| James | Komskom | ||
| Luke | FinkNode | ||
| Myles | MiloNode | ||
| Richard | ClearV | ||
| Ruald | Psypher1 | ||
IP Addresses
| Network | Status | Allocated To | Function |
|---|---|---|---|
| 172.18.87.0/28 | Active | Aragon | Backbone |
| 172.18.87.16/28 | Reserved | Aragon | Future growth or new allocations |
| 172.18.87.32/29 | Active | David | Backbone |
| 172.18.87.40/29 | Reserved | David | Future growth or new allocations |
| 172.18.87.48/29 | Active | Georg | Backbone |
| 172.18.87.56/29 | Reserved | Georg | Future growth or new allocations |
| 172.18.87.64/27 | Active | Georg | Home LAN |
| 172.18.87.96/28 | Active | Luke | Home LAN |
| 172.18.87.112/28 | Active | Ruald | Home LAN |
| 172.18.87.128/28 | Active | Aragon | Home LAN |
| 172.18.87.144/28 | Active | Armand | Second Home LAN |
| 172.18.87.160/28 | Active | James | Home LAN |
| 172.18.87.176/28 | Unallocated | ||
| 172.18.87.192/28 | Active | Myles | Home LAN |
| 172.18.87.208/28 | Active | Armand | Home LAN |
| 172.18.87.224/28 | Active | David | Home LAN |
| 172.18.87.240/28 | Active | Cobus | Home LAN |
| 172.18.88.0/24 | Unallocated |
Frequency Usage
| Access Point | Frequency | Width | Polarisation | TX Level | Ant Gain | Function |
|---|---|---|---|---|---|---|
| Republic | 5220 MHz | 40 MHz (+) | Horizontal | 14 dBm | 31 dBi | PtP |
| Vertex | 5620 MHz | 40 MHz (+) | Hor. + Vert. | 15 dBm | 17 dBi | PtMP |
| Kush | 5540 MHz | 40 MHz (+) | Hor. + Vert. | 12 dBm | 16 dBi | PtMP |
| HitmanV-AP | 5805 MHz | 40 MHz (-) | Hor. + Vert. | 9 dBm | 22 dBi | PtMP |
| Slangkop-AP | 5500 MHz | 40 MHz (+) | Hor. + Vert. | 18 dBm | 16 dBi | PtMP |
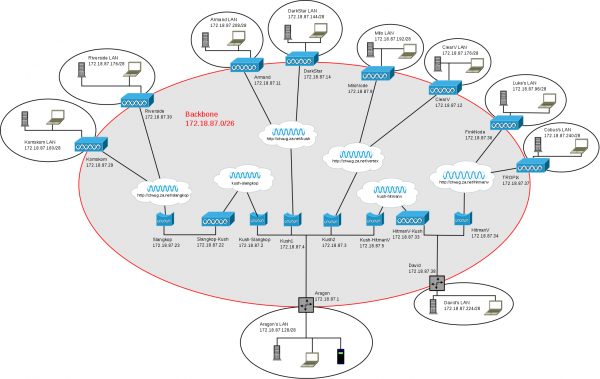
Network Diagram
Unfortunately I'm not able to upload the original Dia source file here, but I'll make this available via another means. Contact me (Aragon) directly if you want a copy in the mean time. Below is a PNG rendering of the diagram.
Network Services
| Address | Protocol | Admin |
|---|---|---|
| 172.18.87.1 | DNS | Aragon |
| adc://hub.hbwug:1511 | ADC | Aragon |
| mumble.hbwug | Mumble | Aragon |
| 172.18.87.68(Inactive) | 25565(MineCraft Server) | Georg |
AirOS Custom Firewall Script
Ubiquiti devices run Linux and use iptables for firewalling. Unfortunately their web interface to iptables is very limited, so in order to run a more advanced ruleset one needs to create a linux shell script that adds firewall rules manually. This is done by SSH'ing to the device and following these instructions to create a /etc/persistent/rc.poststart file. Here is a sample of what I use on a few devices:
#!/bin/sh
PATH=${PATH}:/sbin
LOCALNET="172.18.87.96/28"
WLANIP="172.18.87.36/32"
DCPORT="52000"
iptables -F FIREWALL
iptables -A FIREWALL --protocol icmp -j ACCEPT
iptables -A FIREWALL -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${WLANIP} -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol tcp --dport ${DCPORT} -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol tcp --dport $((${DCPORT}+1)) -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol udp --dport ${DCPORT} -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol udp --dport 33434:65535 -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --protocol tcp -j REJECT --reject-with tcp-reset
iptables -A FIREWALL -i ath0 -j REJECT
To complete things you must:
- Edit LOCALNET to be the subnet address of your LAN listed in the allocations table above.
- Edit WLANIP to be the IP address of your WLAN IP address as configured in your device.
- Enable the firewall in the web interface of your device.
- Configure your DC client as shown below.
This basic ruleset essentially creates a stateful firewall that allows all outgoing connections, all ICMP in both directions, and all incoming DC connections. Any non-DC incoming traffic is blocked, so if you're going to be gaming or doing something that requires incoming connections, you will need to add additional rules for it. Contact Aragon if you need any help.
File Sharing
We use ADC for sharing files on the WUG. You will need an ADC 1.0 compliant client to participate, and we recommend EisKaltDC. Once installed use the following connection settings:
- Mode: Active
- TCP Port: 52000
- UDP Port: 52000
- TLS Port: 52001
Make sure those ports are open on your respective firewalls (the above AirOS firewall script leaves those ports open).
Then just add the ADC hub listed in Network Services above to your favourites.