Difference between revisions of "Hout Bay"
(Initial Ubiquiti customisations doc) |
|||
| Line 152: | Line 152: | ||
|Georg | |Georg | ||
|} | |} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| Line 205: | Line 168: | ||
| − | == | + | ==Ubiquiti Customisations== |
| + | |||
| + | We use a number of Ubiquiti customisations to make things run smoother on HBWUG. The following instructions are intended for wuggers with some networking and Unix knowledge. All the changes below need to be done on the command line of your device via SSH. | ||
| + | |||
| + | ===Step 1: Setup shell profile=== | ||
| + | This is primarily a cosmetic improvement, but a very useful one. Add the following to '''/etc/persistent/profile''': | ||
| + | |||
| + | <pre> | ||
| + | PS1='\[\e]1;\h-term\a\e]2;\h:\w\a\]\h\$ ' | ||
| + | </pre> | ||
| + | |||
| + | ===Step 2: Setup OSPF=== | ||
| + | This requires custom Ubiquiti firmware. Either obtain a precompiled image from Aragon or build one yourself by following: [[Adding OSPF support to Ubiquiti devices]]. | ||
| + | |||
| + | Once you've loaded OSPF firmware on your device, create a BIRD configuration in '''/etc/persistent/bird4.conf'''. Here's a sample: | ||
| + | |||
| + | <pre> | ||
| + | log stderr all; | ||
| + | router id 0.0.0.0; | ||
| + | |||
| + | filter ospfin { | ||
| + | if gw ~ 172.18.87.0/26 then { | ||
| + | if net ~ 172.18.87.0/24 then accept; | ||
| + | if net ~ 172.18.88.0/24 then accept; | ||
| + | } | ||
| + | if gw = 172.18.87.20 then { | ||
| + | if net ~ 172.16.0.0/12 then accept; | ||
| + | } | ||
| + | if gw = 172.18.87.1 then { | ||
| + | if net = 0.0.0.0/0 then accept; | ||
| + | } | ||
| + | reject; | ||
| + | } | ||
| + | |||
| + | protocol kernel { | ||
| + | persist; | ||
| + | learn; | ||
| + | description "kernel"; | ||
| + | scan time 300; | ||
| + | import none; | ||
| + | export all; | ||
| + | } | ||
| + | |||
| + | protocol device { | ||
| + | scan time 300; | ||
| + | } | ||
| + | |||
| + | protocol ospf wug { | ||
| + | tick 1; | ||
| + | import filter ospfin; | ||
| + | export all; | ||
| + | description "WUG"; | ||
| + | area 0.0.0.0 { | ||
| + | interface "ath0" { | ||
| + | cost 10; | ||
| + | hello 10; | ||
| + | retransmit 20; | ||
| + | type broadcast; | ||
| + | authentication none; | ||
| + | }; | ||
| + | interface "eth0" { | ||
| + | cost 10; | ||
| + | type broadcast; | ||
| + | stub; | ||
| + | }; | ||
| + | }; | ||
| + | } | ||
| + | </pre> | ||
| + | |||
| + | ===Step 3: Create firewall script=== | ||
| + | Ubiquiti devices run Linux and use [http://linux.die.net/man/8/iptables iptables] for firewalling. Unfortunately their web interface to iptables is very limited, so in order to run a more advanced firewall we add a custom firewall script. | ||
| + | |||
| + | Create '''/etc/persistent/rc.firewall''' with the following contents: | ||
| + | |||
| + | <pre> | ||
| + | DCPORT="2222" | ||
| + | |||
| + | iptables -F FIREWALL | ||
| + | iptables -A FIREWALL --protocol icmp -j ACCEPT | ||
| + | iptables -A FIREWALL -m state --state ESTABLISHED,RELATED -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst ${WLANIP} -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst ${WLANIP} --protocol ospf -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst 224.0.0.5/32 --protocol ospf -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst 224.0.0.6/32 --protocol ospf -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst 224.0.0.22/32 --protocol igmp -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol tcp --dport ${DCPORT} -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol tcp --dport $((${DCPORT}+1)) -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol udp --dport ${DCPORT} -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol udp --dport 33434:65535 -m state --state NEW -j ACCEPT | ||
| + | iptables -A FIREWALL -i ath0 --protocol tcp -j REJECT --reject-with tcp-reset | ||
| + | iptables -A FIREWALL -i ath0 --dst 255.255.255.255 --protocol udp --dport 5678 -j DROP | ||
| + | iptables -A FIREWALL -i ath0 -j REJECT | ||
| + | </pre> | ||
| + | |||
| + | Also remember to: | ||
| + | |||
| + | * Enable the firewall in the web interface of your device. | ||
| + | * Configure your DC client as shown [[#File_Sharing|below]]. | ||
| + | |||
| + | ===Step 4: Create boot time HBWUG scripts=== | ||
| + | This step creates the necessary boot time code that allows Step 2 and 3 to work. Create the following files: | ||
| + | |||
| + | '''/etc/persistent/config.php''': | ||
| + | <pre> | ||
| + | #!/bin/cgi -q | ||
| + | <? | ||
| + | chdir("/usr/www"); | ||
| + | include("lib/settings.inc"); | ||
| + | $cfg = @cfg_load($cfg_file); | ||
| + | if ($cfg == -1) { exit; } | ||
| + | $netmode = cfg_get($cfg, "netmode"); | ||
| + | $fwstatus = cfg_get($cfg, "iptables.status"); | ||
| + | $lannet = cfg_get($cfg, "netconf.1.ip") + "/" + cfg_get($cfg, "netconf.1.netmask"); | ||
| + | $wlanip = cfg_get($cfg, "netconf.2.ip"); | ||
| + | $bridgeip = cfg_get($cfg, "netconf.3.ip"); | ||
| + | echo("NETMODE=\"$netmode\"\n"); | ||
| + | echo("FWSTATUS=\"$fwstatus\"\n"); | ||
| + | echo("LOCALNET=\"$lannet\"\n"); | ||
| + | echo("WLANIP=\"$wlanip\"\n"); | ||
| + | echo("BRIDGEIP=\"$bridgeip\"\n"); | ||
| + | ?> | ||
| + | BIRDENABLE=1 | ||
| + | OSPFDEFROUTE=1 | ||
| + | </pre> | ||
| + | |||
| + | '''/etc/persistent/rc.hbwug''': | ||
| + | <pre> | ||
| + | #!/bin/sh | ||
| + | |||
| + | eval "$(/etc/persistent/config.php)" | ||
| + | PATH=${PATH}:/sbin | ||
| + | |||
| + | case "$1" in | ||
| + | start) | ||
| + | echo "HBWUG startup" | ||
| + | STARTBIRD=0 | ||
| + | [ -z "${BIRDENABLE}" ] && BIRDENABLE=0 | ||
| + | [ -z "${OSPFDEFROUTE}" ] && OSPFDEFROUTE=0 | ||
| + | BIRDCONF=/etc/persistent/bird4.conf | ||
| + | FWCONF=/etc/persistent/rc.firewall | ||
| + | if [ "${NETMODE}" = "router" ]; then | ||
| + | for f in /proc/sys/net/ipv4/conf/*; do | ||
| + | echo 1 >${f}/accept_redirects | ||
| + | echo 1 >${f}/send_redirects | ||
| + | done | ||
| + | if [ "${FWSTATUS}" = "enabled" -a -e ${FWCONF} ]; then | ||
| + | . ${FWCONF} | ||
| + | fi | ||
| + | if [ ${BIRDENABLE} -eq 1 -a -e ${BIRDCONF} -a -n "${WLANIP}" ]; then | ||
| + | sed -i -e "/^router id/ c router id ${WLANIP};" ${BIRDCONF} | ||
| + | STARTBIRD=1 | ||
| + | fi | ||
| + | elif [ "${NETMODE}" = "bridge" ]; then | ||
| + | if [ ${BIRDENABLE} -eq 1 -a -e ${BIRDCONF} -a -n "${BRIDGEIP}" ]; then | ||
| + | sed -i -e "/^router id/ c router id ${BRIDGEIP};" ${BIRDCONF} | ||
| + | STARTBIRD=1 | ||
| + | fi | ||
| + | fi | ||
| + | if [ ${STARTBIRD} -eq 1 ]; then | ||
| + | if [ ${OSPFDEFROUTE} -eq 1 ]; then | ||
| + | route delete -net 0.0.0.0/0 | ||
| + | fi | ||
| + | /usr/bin/bird4.init start | ||
| + | fi | ||
| + | ;; | ||
| + | stop) | ||
| + | echo "HBWUG shutdown" | ||
| + | /usr/bin/bird4.init stop | ||
| + | ;; | ||
| + | esac | ||
| + | </pre> | ||
| + | |||
| + | '''/etc/persistent/rc.poststart''': | ||
| + | <pre> | ||
| + | /etc/persistent/rc.hbwug start | ||
| + | </pre> | ||
| − | + | '''/etc/persistent/rc.prestop''': | |
| + | <pre> | ||
| + | /etc/persistent/rc.hbwug stop | ||
| + | </pre> | ||
Revision as of 19:35, 30 January 2011
Contents
Hout Bay WUG
The Hout Bay WUG is a historic name for what is now the Hout Bay area on CTWUG. It started life in March 2010 as a Hout Bay specific WUG, disconnected from CTWUG due to geographic hurdles in connecting. On 23 December 2010 it was connected to CTWUG via its only peer, Kommetjie, which established a link to the Noordhoek and Fishoek areas. This Wiki entry is just a knowledge base specific to our area.
Meet the Hout Bay Wuggers
| Name | Nodes | |
|---|---|---|
| Aragon | Kush | |
| Armand | DarkStar | DeathStarCanteen |
| Cobus | TROPiX | |
| David | HitmanV | |
| Denis | d3nis | |
| Georg | Slangkop | Riverside |
| James | Komskom | |
| Luke | FinkNode | |
| Myles | MiloNode | |
| Richard | ClearV | |
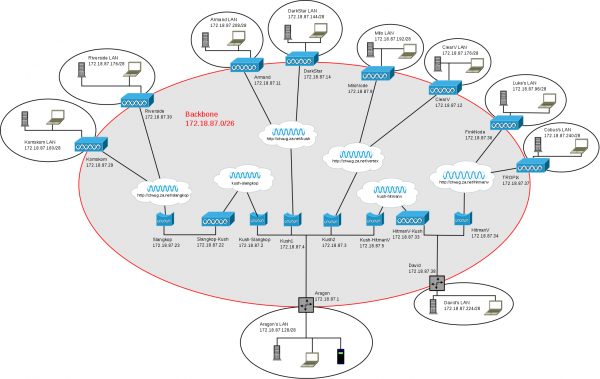
Network Layout
IP Addresses
| Network | Status | Allocated To | Function |
|---|---|---|---|
| 172.18.87.0/26 | Active | HBWUG | Backbone |
| 172.18.87.64/27 | Active | Georg | Home LAN |
| 172.18.87.96/28 | Active | Luke | Home LAN |
| 172.18.87.112/28 | Unallocated | ||
| 172.18.87.128/28 | Active | Aragon | Home LAN |
| 172.18.87.144/28 | Active | Armand | Second Home LAN |
| 172.18.87.160/28 | Active | James | Home LAN |
| 172.18.87.176/28 | Active | Richard | Home LAN |
| 172.18.87.192/28 | Active | Myles | Home LAN |
| 172.18.87.208/28 | Active | Armand | Home LAN |
| 172.18.87.224/28 | Active | David | Home LAN |
| 172.18.87.240/29 | Active | Cobus | Home LAN |
| 172.18.87.248/29 | Unallocated | ||
| 172.18.88.0/24 | Unallocated |
Network Services
| Address | Protocol | Admin |
|---|---|---|
| 172.18.87.1 | DNS | Aragon |
| adc://hub.aragon.ctwug.za.net:1511 | ADC | Aragon |
| mumble://mumble.aragon.ctwug.za.net | Mumble | Aragon |
| minecraft.hbwug:25565 | MineCraft | Georg |
File Sharing
We use ADC for sharing files on the WUG. You will need an ADC 1.0 compliant client to participate, and we recommend EisKaltDC. Once installed use the following connection settings:
- Mode: Active
- TCP Port: 2222
- UDP Port: 2222
- TLS Port: 2223
Make sure those ports are open on your respective firewalls (the above AirOS firewall script leaves those ports open).
Then just add the ADC hub listed in Network Services above to your favourites.
Ubiquiti Customisations
We use a number of Ubiquiti customisations to make things run smoother on HBWUG. The following instructions are intended for wuggers with some networking and Unix knowledge. All the changes below need to be done on the command line of your device via SSH.
Step 1: Setup shell profile
This is primarily a cosmetic improvement, but a very useful one. Add the following to /etc/persistent/profile:
PS1='\[\e]1;\h-term\a\e]2;\h:\w\a\]\h\$ '
Step 2: Setup OSPF
This requires custom Ubiquiti firmware. Either obtain a precompiled image from Aragon or build one yourself by following: Adding OSPF support to Ubiquiti devices.
Once you've loaded OSPF firmware on your device, create a BIRD configuration in /etc/persistent/bird4.conf. Here's a sample:
log stderr all;
router id 0.0.0.0;
filter ospfin {
if gw ~ 172.18.87.0/26 then {
if net ~ 172.18.87.0/24 then accept;
if net ~ 172.18.88.0/24 then accept;
}
if gw = 172.18.87.20 then {
if net ~ 172.16.0.0/12 then accept;
}
if gw = 172.18.87.1 then {
if net = 0.0.0.0/0 then accept;
}
reject;
}
protocol kernel {
persist;
learn;
description "kernel";
scan time 300;
import none;
export all;
}
protocol device {
scan time 300;
}
protocol ospf wug {
tick 1;
import filter ospfin;
export all;
description "WUG";
area 0.0.0.0 {
interface "ath0" {
cost 10;
hello 10;
retransmit 20;
type broadcast;
authentication none;
};
interface "eth0" {
cost 10;
type broadcast;
stub;
};
};
}
Step 3: Create firewall script
Ubiquiti devices run Linux and use iptables for firewalling. Unfortunately their web interface to iptables is very limited, so in order to run a more advanced firewall we add a custom firewall script.
Create /etc/persistent/rc.firewall with the following contents:
DCPORT="2222"
iptables -F FIREWALL
iptables -A FIREWALL --protocol icmp -j ACCEPT
iptables -A FIREWALL -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${WLANIP} -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${WLANIP} --protocol ospf -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst 224.0.0.5/32 --protocol ospf -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst 224.0.0.6/32 --protocol ospf -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst 224.0.0.22/32 --protocol igmp -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol tcp --dport ${DCPORT} -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol tcp --dport $((${DCPORT}+1)) -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol udp --dport ${DCPORT} -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --dst ${LOCALNET} --protocol udp --dport 33434:65535 -m state --state NEW -j ACCEPT
iptables -A FIREWALL -i ath0 --protocol tcp -j REJECT --reject-with tcp-reset
iptables -A FIREWALL -i ath0 --dst 255.255.255.255 --protocol udp --dport 5678 -j DROP
iptables -A FIREWALL -i ath0 -j REJECT
Also remember to:
- Enable the firewall in the web interface of your device.
- Configure your DC client as shown below.
Step 4: Create boot time HBWUG scripts
This step creates the necessary boot time code that allows Step 2 and 3 to work. Create the following files:
/etc/persistent/config.php:
#!/bin/cgi -q
<?
chdir("/usr/www");
include("lib/settings.inc");
$cfg = @cfg_load($cfg_file);
if ($cfg == -1) { exit; }
$netmode = cfg_get($cfg, "netmode");
$fwstatus = cfg_get($cfg, "iptables.status");
$lannet = cfg_get($cfg, "netconf.1.ip") + "/" + cfg_get($cfg, "netconf.1.netmask");
$wlanip = cfg_get($cfg, "netconf.2.ip");
$bridgeip = cfg_get($cfg, "netconf.3.ip");
echo("NETMODE=\"$netmode\"\n");
echo("FWSTATUS=\"$fwstatus\"\n");
echo("LOCALNET=\"$lannet\"\n");
echo("WLANIP=\"$wlanip\"\n");
echo("BRIDGEIP=\"$bridgeip\"\n");
?>
BIRDENABLE=1
OSPFDEFROUTE=1
/etc/persistent/rc.hbwug:
#!/bin/sh
eval "$(/etc/persistent/config.php)"
PATH=${PATH}:/sbin
case "$1" in
start)
echo "HBWUG startup"
STARTBIRD=0
[ -z "${BIRDENABLE}" ] && BIRDENABLE=0
[ -z "${OSPFDEFROUTE}" ] && OSPFDEFROUTE=0
BIRDCONF=/etc/persistent/bird4.conf
FWCONF=/etc/persistent/rc.firewall
if [ "${NETMODE}" = "router" ]; then
for f in /proc/sys/net/ipv4/conf/*; do
echo 1 >${f}/accept_redirects
echo 1 >${f}/send_redirects
done
if [ "${FWSTATUS}" = "enabled" -a -e ${FWCONF} ]; then
. ${FWCONF}
fi
if [ ${BIRDENABLE} -eq 1 -a -e ${BIRDCONF} -a -n "${WLANIP}" ]; then
sed -i -e "/^router id/ c router id ${WLANIP};" ${BIRDCONF}
STARTBIRD=1
fi
elif [ "${NETMODE}" = "bridge" ]; then
if [ ${BIRDENABLE} -eq 1 -a -e ${BIRDCONF} -a -n "${BRIDGEIP}" ]; then
sed -i -e "/^router id/ c router id ${BRIDGEIP};" ${BIRDCONF}
STARTBIRD=1
fi
fi
if [ ${STARTBIRD} -eq 1 ]; then
if [ ${OSPFDEFROUTE} -eq 1 ]; then
route delete -net 0.0.0.0/0
fi
/usr/bin/bird4.init start
fi
;;
stop)
echo "HBWUG shutdown"
/usr/bin/bird4.init stop
;;
esac
/etc/persistent/rc.poststart:
/etc/persistent/rc.hbwug start
/etc/persistent/rc.prestop:
/etc/persistent/rc.hbwug stop